Configuring AuthLite to use your Group Pairs
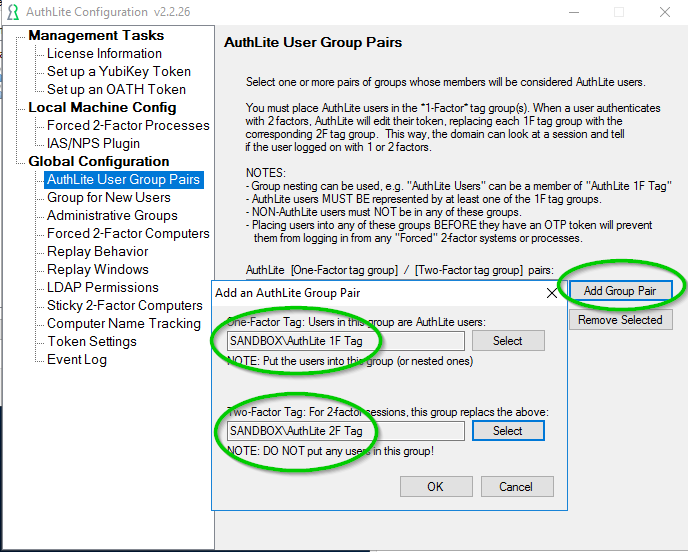
Configure AuthLite to use your 1F and 2F tag groups as shown in Figure 1.
This dialog does two separate things:
1) Identifies AuthLite Users
Users who have nested membership in any of these groups are treated as being AuthLite Users. Any user who is not included in these groups will never be enforced or blocked by AuthLite.
Note: simply being in the AuthLite Users group or having a token does not require you to use 2-factor login anywhere. You need to set up Enforcement too!
2) Enables AuthLite to tag sessions as 1 or 2-factor
Each AuthLite user is naturally a member of the 1-Factor Session Tag group (remember on the previous step we made AuthLite Users a member of AuthLite 1-Factor Session Tag? That's why). This is our way of saying, "If you see a logon of this user, assume it is 1-factor until AuthLite says otherwise."
When the user logs on with an OTP token, AuthLite will do a "search and replace" on their logon session, swapping the 1-Factor Session Tag group out, and adding the 2-Factor Session Tag group in its place. This way, systems and policies that examine the session can tell whether the user logged on with their token or not. This is the fundamental basis of how AuthLite's permission controls work.
"But I want 2-factor users, shouldn't I put them in the '2-Factor Session Tag' ?"
No, definitely not! If you place users in the 2-Factor Session Tag group, then (even when they don't use their token) AuthLite and all your systems will believe they used 2-factors even when they didn't. This totally breaks the security model AuthLite is trying to use. For most configurations, your 2-Factor Session Tag groups should be empty of members, and stay that way. They will just be added to sessions dynamically by AuthLite.