Watchguard NPS settings
New RADIUS client
Connection Request Policies
New Network Policy
Windows Groups
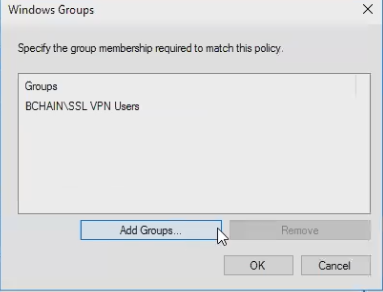
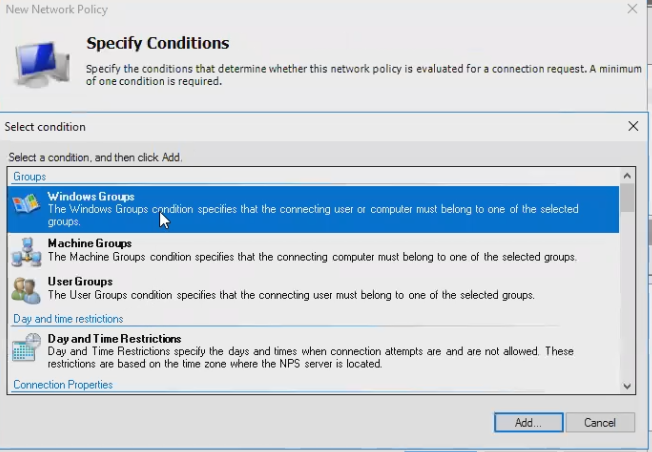
Select group(s)
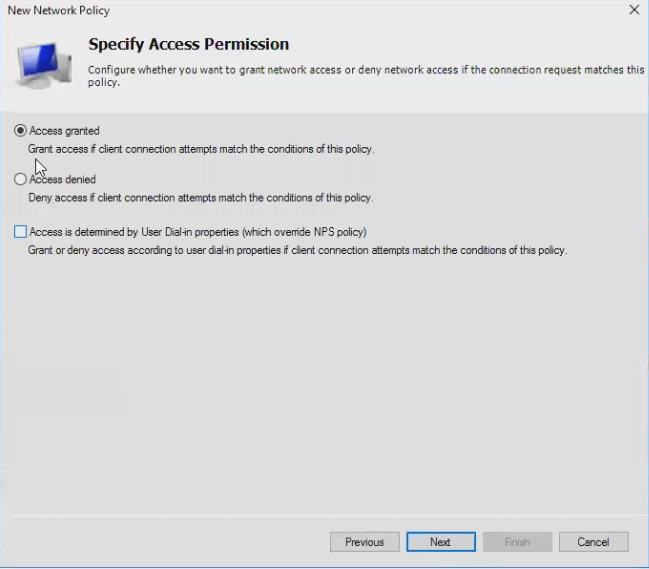
Grant access
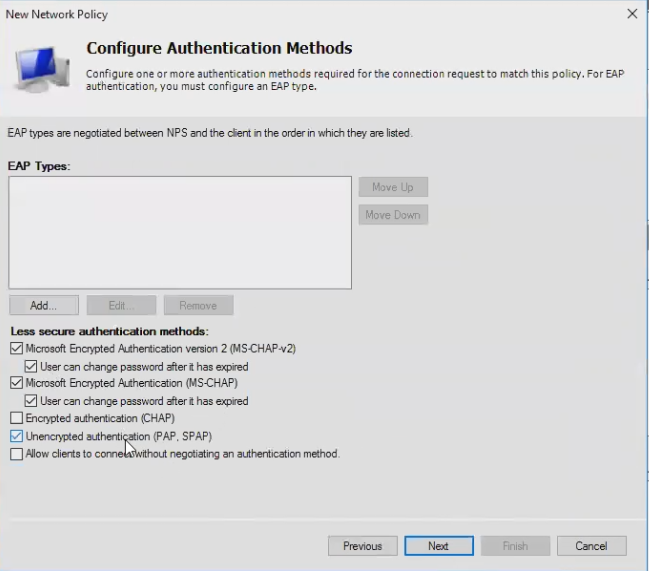
Add PAP
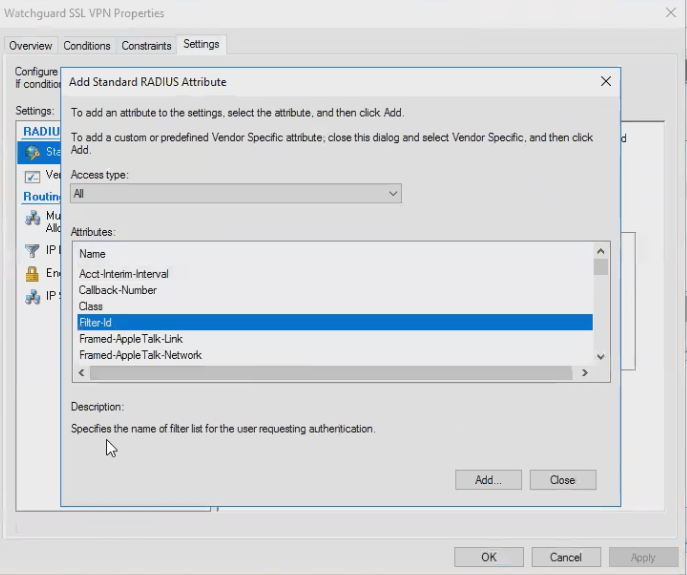
Add Filter-Id
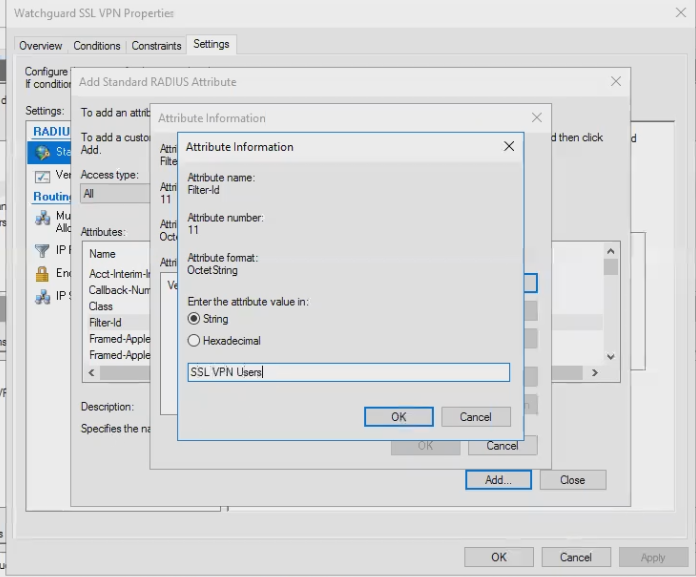
Filter-Id = Watchguard group string
- Install the NPS role and the Network Policy Server feature on one or more member servers or DCs
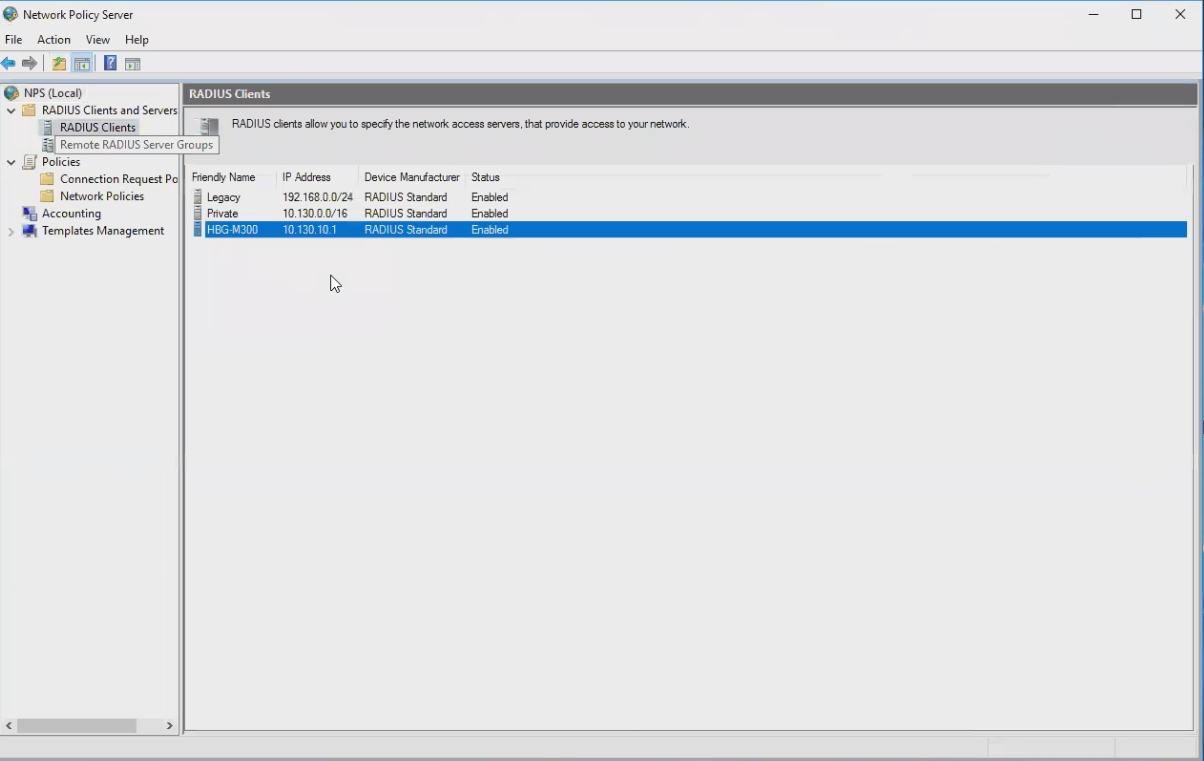
- In the Network Policy Server administrative tool, add a RADIUS client
- It should match the *LAN* IP Address of your Watchguard, i.e. the IP address that will communicate to the RADIUS server
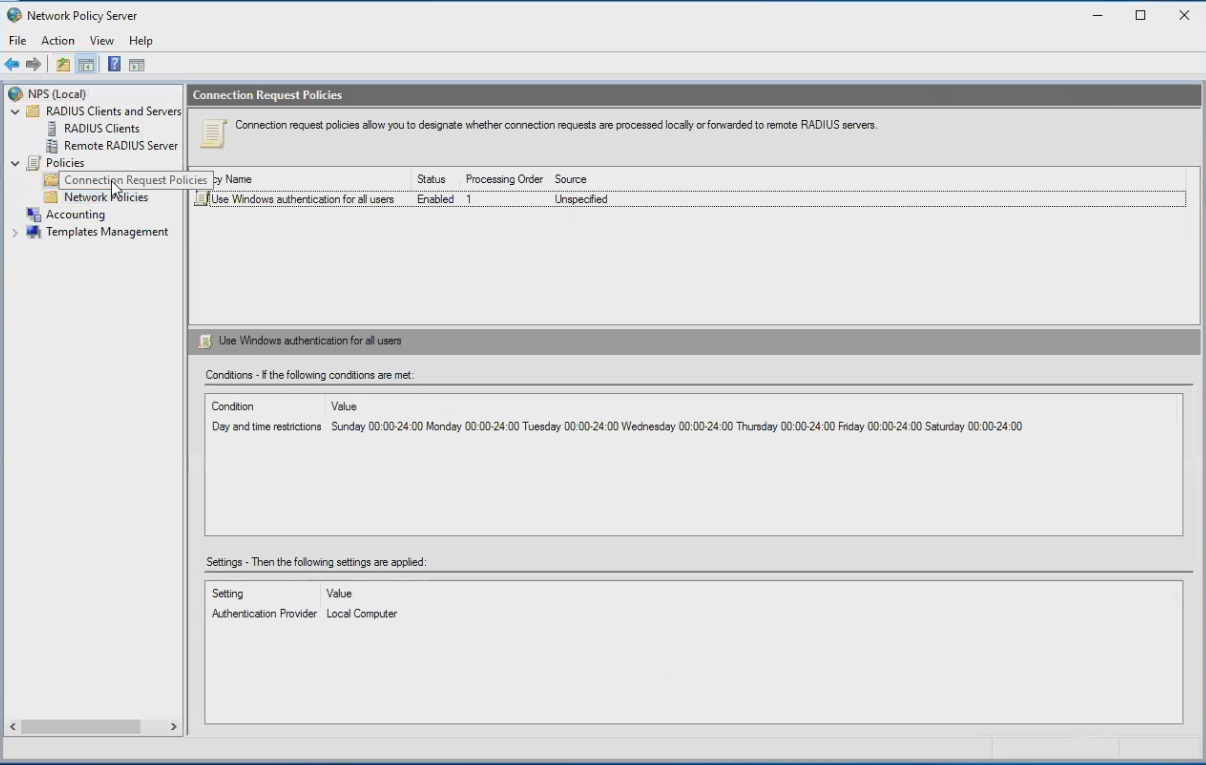
- Make sure Connection Request Policies has "Use Windows authentication for all users" (default)
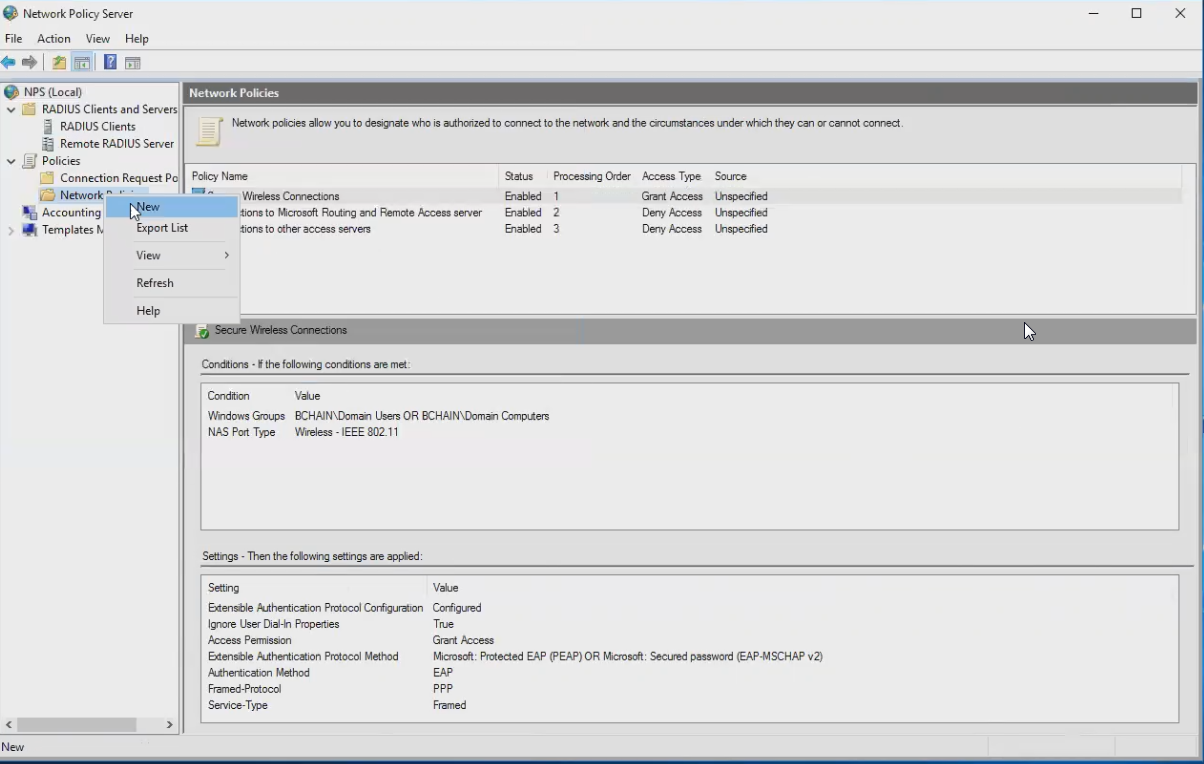
- Create a new Network Policy for the watchguard VPN
- Set a condition for the AD group(s) you would like to match to allow VPN access
- Specify Access Granted
- Add "Unencrypted authentication (PAP, SPAP)
Note: it is not *really* unencrypted; that dialog message is a hold-over from the old PPTP days when the tunnel security was tied to the password hashing protocol. These days the tunnel is encrypted by SSL, and the communication between the Watchguard and the RADIUS server is encrypted by the RADIUS shared secret.
- In the Constraints dialog add a "Standard RADIUS Attribute"
- Select Filter-Id
- Enter the exact same string here that you set for the Group name *in the Watchguard* earlier, i.e. "SSL VPN Users". This string doesn't necessarily correspond to an AD group, it is just the value that the Watchguard is set to look for
